19. Exercise Solution: Penetration Testing
Exercise Solution: Penetration Testing
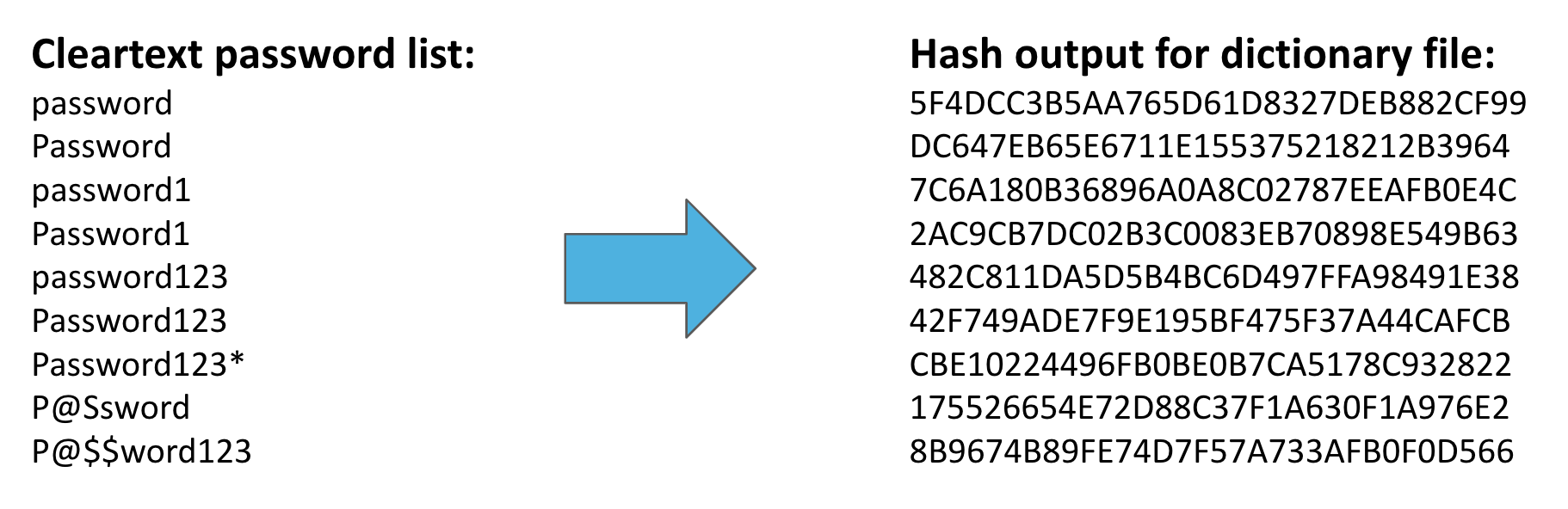
You’ve been tasked with generating a password dictionary for your attack. This is basically a hashed list of common passwords you can use to try to match up a password.
There are tools and scripts that can be written to automate this as you advance, however we’ll create the list manually so that you fundamentally understand how password cracking works. Let’s say the base keyword you choose is “password”. You’d create variations based on that because people tend to use common words and then add a few numbers or special characters. So, if you know your targets favorite color, or kids name, and other details like that this list can grow to include all kinds of combinations you might come up with, but here’s my example for the base word password.
Cleartext password list:
password
Password
password1
Password1
password123
Password123
Password123*
P@Ssword
P@$$word123
Also, if you know what the required length, casing, number, and special character rules are, you can create a more efficient list as an attacker.
Now that you have this list, it’s still not all you need. Remember that systems don't typically store passwords in clear text. Once you have your list of passwords you think might be right, you’ll need to hash them.
Here’s example hash output using MD5 hashing.
5F4DCC3B5AA765D61D8327DEB882CF99
DC647EB65E6711E155375218212B3964
7C6A180B36896A0A8C02787EEAFB0E4C
2AC9CB7DC02B3C0083EB70898E549B63
482C811DA5D5B4BC6D497FFA98491E38
42F749ADE7F9E195BF475F37A44CAFCB
CBE10224496FB0BE0B7CA5178C932822
175526654E72D88C37F1A630F1A976E2
8B9674B89FE74D7F57A733AFB0F0D566
FD32F63A223767E782A003C7985AF225
That becomes your dictionary file for the attack. In practice you’ll want to automate this with a script, use a rule based attack, or leverage existing dictionary files and functions already existing within password cracking tools. For example, there are some default dictionaries included in HashCat.